On February 21, 2025, bybit, a Prominent Cryptocurrency Exchange, Experienced a significant Security Breach Resulting in the loss of Nearly $ 1.5 Billion Worth of Ether (ETH). This incident Stands as the Large Digital Heist in the History of Cryptocurrency. Fortunately, bybit is Actively Collaborating With Industry Experts, Including Chainalysis, To Trace the Stolen Assets. They have also launched a recovery bounty program, offering up to 10% of the recovered love to individuals who assist in retrieving the stolen crypto.
In this blog, we'll look at how the exploit occurred; The Attackers' Tactics, Techniques, and Procedures (TTPS) and their consistency with the Democratic people's republic of Korea (DPRK); and how chainalysis is collaborating with bybit and law enlightenment to help recover funds.
Details of the Bybit exploit
The bybit Hack Serves as a Stark Reminder of the Evolving Tactics Employed by State-Sponsored Cybercriminals, Particularly Those Linked to the Dprk. As we recently revealed in our 2025 Crypto Crime Report, North Korea-Affiliated Hackers Stole Approximataly $ 660.5 million across 20 Incidents in 2023. In 2024, this number Increased to $ 1.34 Billion Stolen across 47 Incidents-A 102.88% Increase in Value Stolen. The bybit Hack Alone Led to Almost $ 160 million More Stolen Than All Funds Stolen by North Korea Throughout 2024.
This attack Highlights A Common Playbook use by the DPRK: Social Orchestracting Engineering Attacks and Employing Intricate Laundering Methods in an attempt to move Stolen funds undeteted. Funds from the bybit exploit have also consolidated in addresses holding funds from other known dprk-linked attacks, Providing Further Evidence That the Nation State Actors Are Behind this latest incident.
Below is a step-by-step analysis of how the bybit UNFOLDED exploit:
- : The Hackers Gained Access to Bybit's User Interface by Executing Phishing Attacks Against The Cold Wallet Signs, Leading Them to Sign Malicious Transactions that replaced the Safe's Multi-Signature Wallet Wallet Implementation Contract with a Malicious One.
- Initiation of unauthorized transfers: DURING what appeal to be a routine transfer from bybit's ethereum cold wallet to a hot wallet, the attackers intercepted the process. They are managed to reroute approximately 401,000 ETH – VALUED AT NEARLY $ 1.5 Billion at the time of the exploit – todresses under their control.
- Asset dispersion through intermediary wallets: The Stolen Fiests Were then Moved Through A Complex Web of Intermediary Addresses. This dispersion is a common tactic used to obfuscate the trail and hinder tracking efforts by blockchain analysts.
- Conversion and laundering: The Hackers Swedpped significant portions of the Stolen Eth for Tokens include BTC and Dai. They also Utilized decentralized Exchanges (Dexs), Cross-Chain Bridges, and a No-Kyc Instant Swap Service To Move Assets Across Networks.
- Keeping funds sleeping and strategic laundering: A notable portion of the stolen funds has remained idle across various addresses, a deliberate move often employed by north korea-abffiliated hackers. By Delaying Laundering Efforts, they like to outlast the heightned show that typalyly Immondelly follows Such High-Profile Breaches.
The Below Chainalysis Reactor Graph Showcases The Complexity of the Laundering Efforts Thus Far: The Web of Intermediary Addresses, Token Swaps, and Cross-Chain Movements that not only attempt to obscure the Stolen Funds, but also demonstrate the Far-Reaching Concuquences of this exploit. across the Broader Crypto Ecosystem.
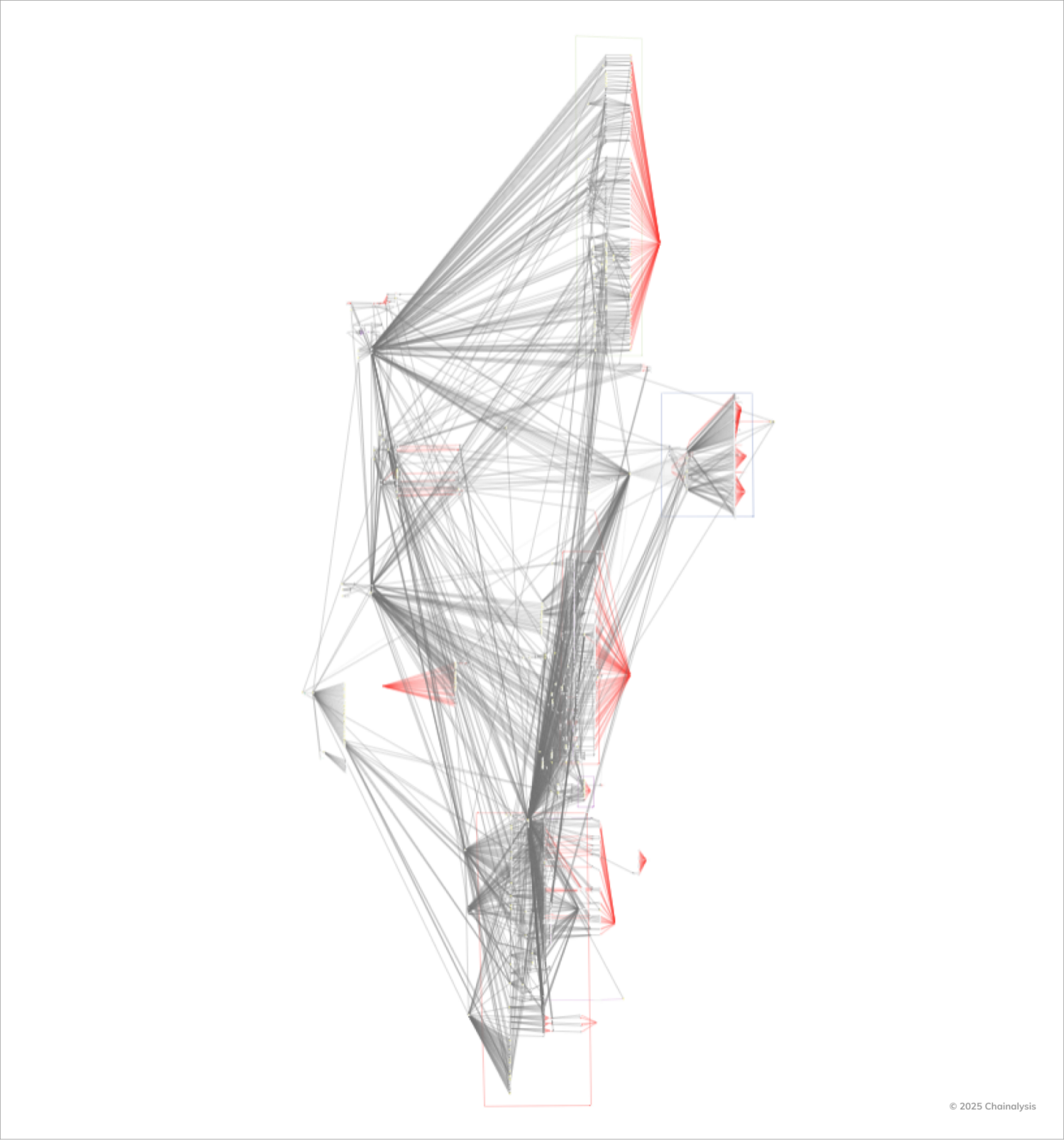
Industry collaboration in the wake of the bybit hack
Despite the Severity of Bybit's Attack, the inherent Transparency of Blockchain Technology Presents a significant Challenge for Malicious Actors Attempting to Launder Stolen Funds. Every Transaction is Recorded on Public Ledger, EnaBubling Authorities and cybersecurity firms to trace and monitor illegit activities in real time.
Collaboration across the crypto ecosystem is paramount in combating these threats. The Swift Responsible from bybit, Including its Insurance to Cover Customer Losses and its Commitment with Blockchain Forensic Experts, Exemplifies The Industry's Commitment to Mutual Support and Resilience. By Uniting Resources and Intelligence, The Crypto Community Can Strengthen Its Defenses Against Such Sophisticated Cyber Attacks and Work Toward A More Secure Digital Financial Environment.
We are working with our global teams, Customers, and Partners Across Both the Public and Private Sectors to Support Multiple Avenues for Seizure and Recovery in Responsible to this Attack. Already, we've worked with contacts in the industry to help freeze more than $ 40 million in funds stolen from bybit and continuing to collaborate with public and private sector organizations to seize as much as possible. We Will Continue to Provide Updates on this Matter.
This Material is for Informational Purposses Only, and is not intended to take legal, tax, financial, or investment advice. Should Should Consult Their Own Advisors Before Making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with container's use of this material.
Chainalysis dues not guaranto or warrant the accuracy, Completeness, Timeliness, follow -up or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such matterial.







