As we’ve covered previously, 2022 was the biggest year in crypto hacking history, with more than $3.8 billion stolen. However, not all of those attacks were what one may think of as hacks in the traditional sense. In some cases, bad actors were able to drain DeFi protocols of funds without actually taking advantage of an error in the protocol’s code. These attackers were able to do this by manipulating the price oracles DeFi protocols use to ensure the assets available on their platforms are priced in accordance with the wider cryptocurrency market. As such, we’ll refer to these unique instances as oracle manipulation attacks.
Bad actors typically carry out oracle manipulation attacks by using large amounts of cryptocurrency to quickly increase the trading volume of low-liquidity tokens on the targeted DeFi protocol, which can lead to fast, significant price increases not reflective of the wider market. Those initial funds are often sourced through a flash loan if the attacker doesn’t have the funds on hand. Once an asset’s price has been driven up, the attacker can then exchange their artificially inflated holdings for other tokens with greater liquidity and a more consistent value, or use them as (worthless) collateral to borrow assets, never to be repaid.
Overall, we estimate that in 2022, DeFi protocols lost $386.2 million in 41 separate oracle manipulation attacks.
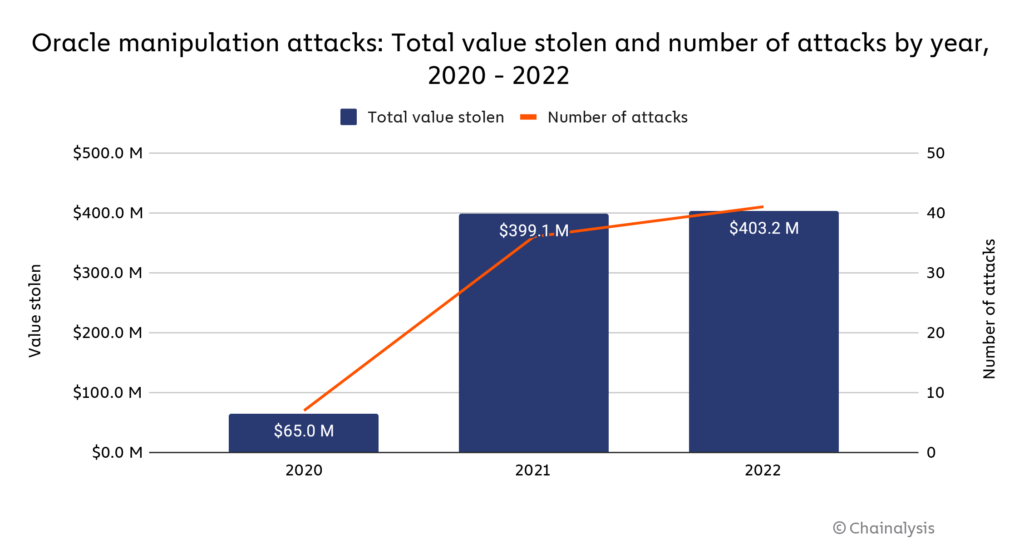
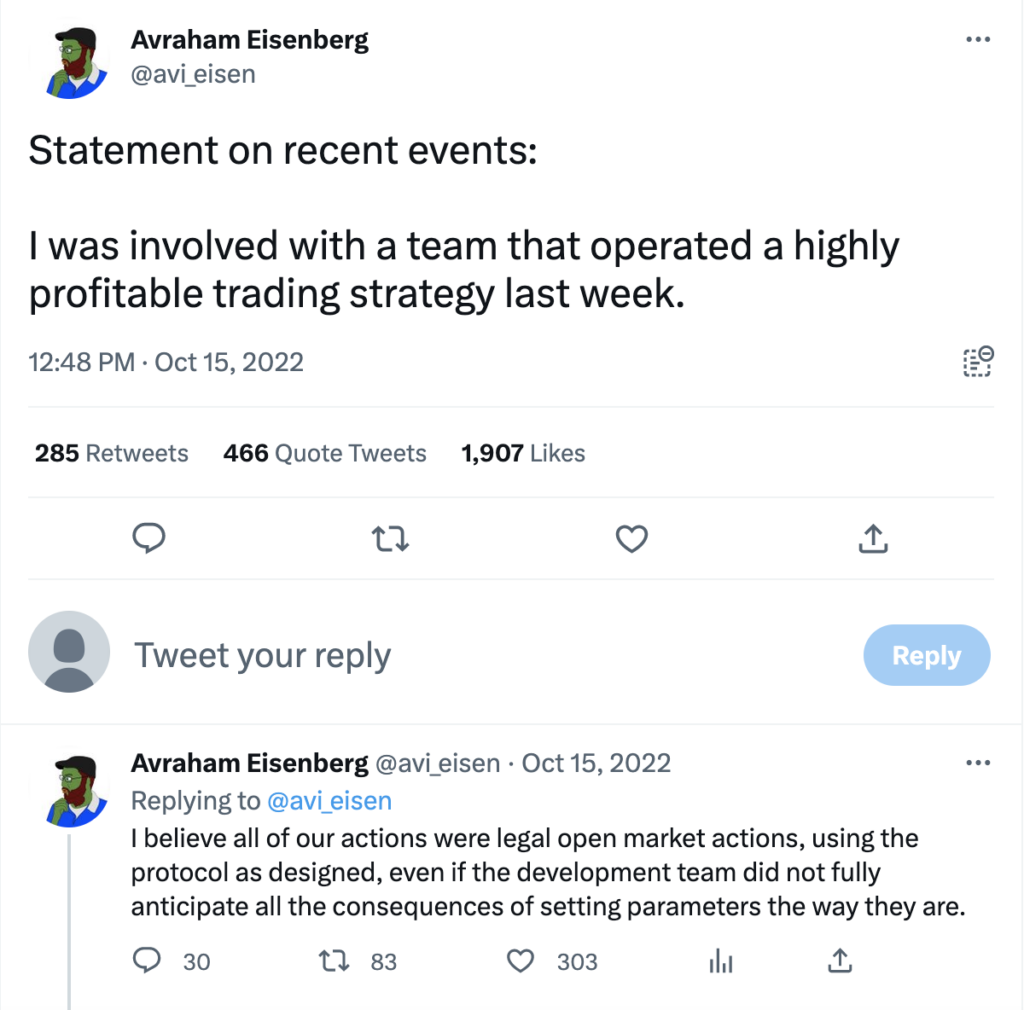
Some attackers have tried to argue that oracle manipulation attacks aren’t criminal in the same way a more straightforward hack is. In fact, Avraham Eisenberg, the individual behind one of the biggest oracle manipulation attacks of the year, claimed that his actions were perfectly legal and represented nothing more than a “profitable trading strategy.” However, the DRY and CFTC both filed charges of market manipulation against him, with the DOJ also bringing an indication. While the trial hasn’t happened yet, the complaint suggests that authorities won’t allow these attackers to evade responsibility, even if the targeted protocol technically behaved as designed. Below, we’ll look at Eisenberg’s infamous million attack on Mango Markets as an example of how oracle manipulation attacks can work.
Breaking down Avraham Eisenberg’s Mango Markets feat
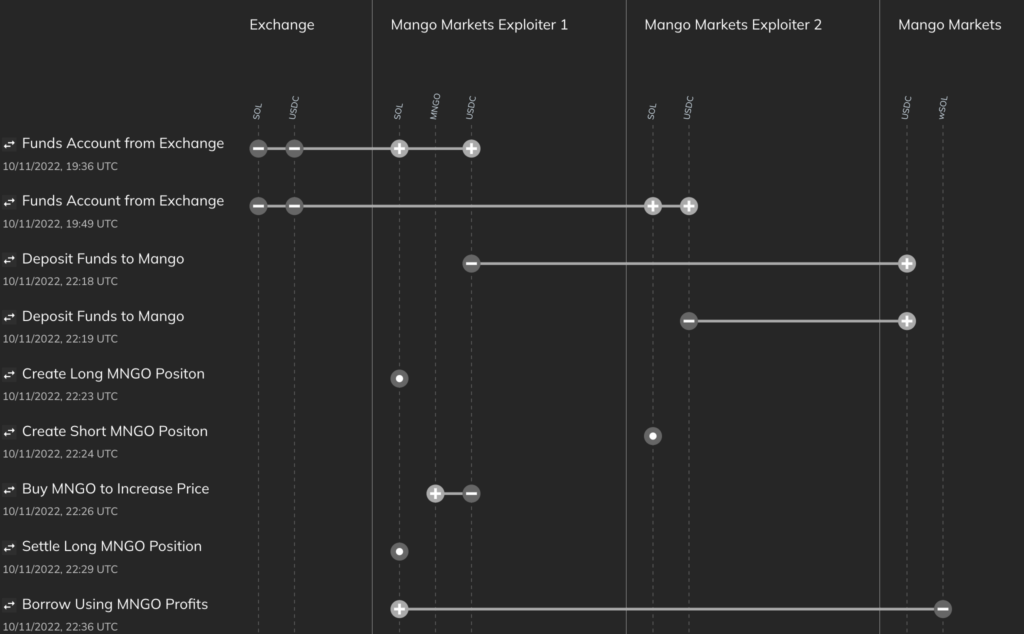
One of the biggest oracle manipulation attacks of last year was the October 2022 attack of Mango Markets, a DEX on the Solana blockchain, which saw $117 million in assets drained from the protocol. The Mango Markets exploit was particularly interesting in that the perpetrator, Avraham Eisenberg, identified himself publicly afterwards and argued that his actions didn’t constitute a crime. Here’s how the exploit occurred from an on-chain perspective:
- Eisenberg started with $10 million USDC (it’s possible he also used funds not attributable to him on-chain to manipulate asset prices on other exchanges), split across two separate accounts at Mango Markets.
- Eisenberg used one account to short 488 million MNGO (MNGO, or Mango, is the governance token for Mango Markets) — effectively selling 488 million MNGO on leverage — while the other account took the opposite side of that trade, using leverage to buy the same amount.
- Eisenberg’s leveraged purchase of MNGO, combined with further buying of MNGO on other DEXes, pushed the price of MNGO up very quickly on spot exchanges. This was possible because MNGO was a low-liquidity asset without much trading volume. The account used to purchase MNGO immediately profited roughly $400 million in paper gains because all of Eisenberg’s buying activity significantly boosted the asset’s price.
- With such a high portfolio value, Eisenberg was able to borrow against his artificially inflated MNGO holdings and remove virtually all of the assets held by Mango Markets. This activity caused MNGO’s price to drop immediately, so his long positions were liquidated due to loss of collateral value, but it was too late — Eisenberg had already “borrowed” all of Mango Market’s assets with any real value.
We can see this activity on the Chainalysis Storyline below:
Adding insult to injury, Eisenberg used the MNGO he still held after the exploit to propose and vote on a governance proposal that would allow him to return $10 million worth of cryptocurrency stolen in the attack, and keep the rest as a “bug bounty.” The proposal eventually passed. While most hackers avoid publicity, Eisenberg was open about his role in the Mango Markets exploit, and seemed convinced that because the code had at all times technically run as designed, he had done nothing wrong. Hey even appeared on Laura Shin’s popular Unchained Podcast to explain this perspective.
However, as the SEC lay out in its complaint, Eisenberg’s actions allegedly qualify as market manipulation due to the false increase in MNGO trading volume — 2,000% higher on the day of the exploit compared to the average over the previous ten days — that he orchestrated. Since charges were filed, Mango Markets has also Sweden Eisenberg for the difference between what he stole and what he returned as a result of his governance proposal, arguing that Eisenberg was not engaged in “lawful bargaining” when he negotiated his bug bounty with the Mango Markets DAO.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.














