Lately, the bull market has fostered a renewed interest in airdrops. These cryptocurrency donations, offered to the first users of a Web3 protocol, are facing a massive wave of phishing on social networks. To ensure your security and that of your cryptocurrencies, here is a list of tips to know to recover your airdrops with maximum security.
Airdrops: beware of hacking risks
When you are a beginner, Airdrop hunting is a good way to learn about blockchain while building capital in cryptocurrencies. However, malicious people take advantage of investors' naivety to steal their cryptocurrencies. How do they do it?
🔎 What is a cryptocurrency airdrop and how to be eligible?
Their main strategy is to usurp the identity of companies in the sector on social networks. By using their visual codes (logo, banner, name, certification), They gain the trust of the most gullible Internet users.
For example, when Blast protocol announced its airdrop on Twitter, followed by its link to claim it, A faker with the same visual identity has created many similar postsSeeking to attract as many investors as possible to his fake site through phishing, his goal is to obtain wallet authorizations to recover the cryptocurrencies stored there.
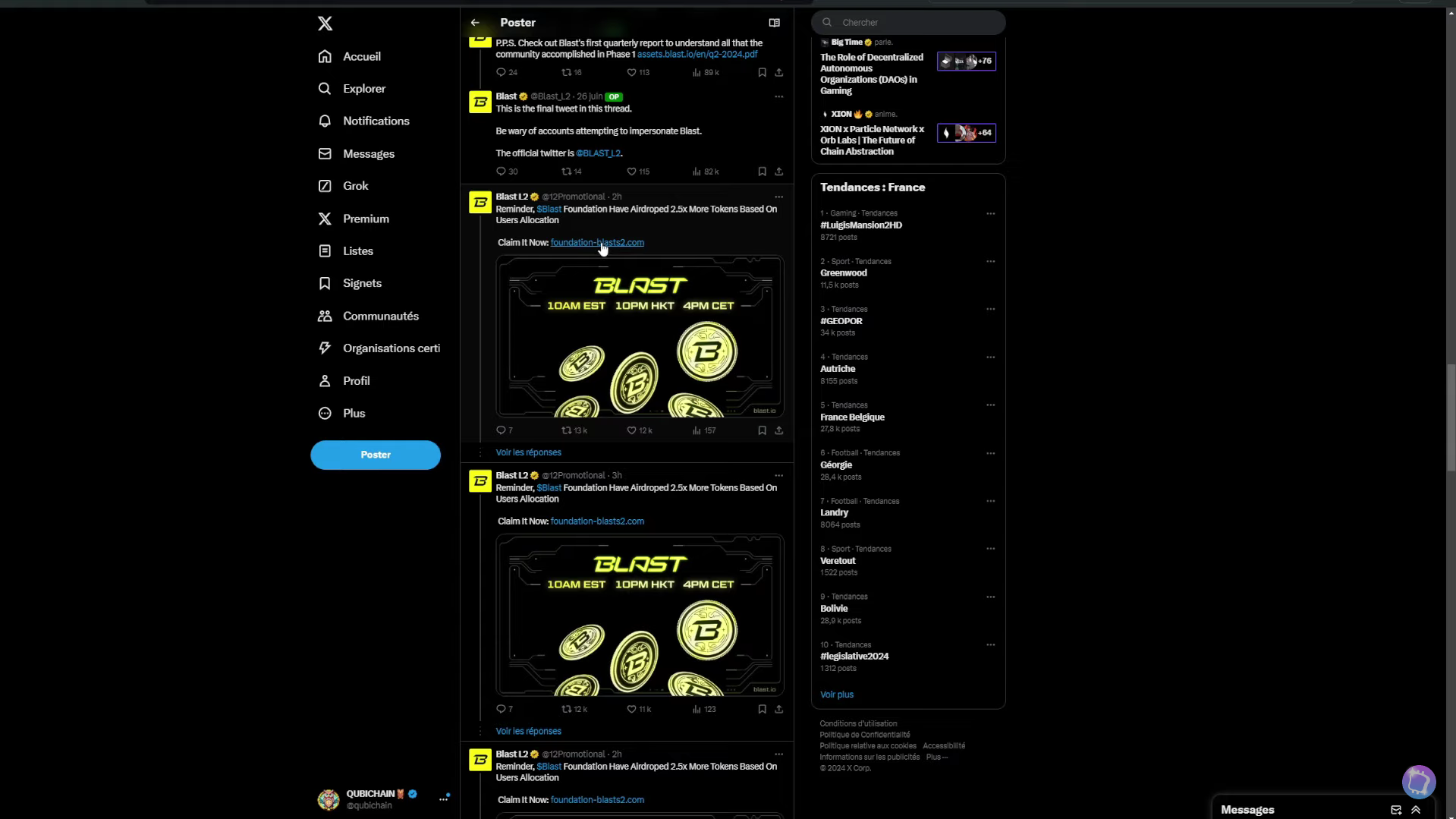
Twitter – Comparison between the official Blast L2 X account (@Blast_L2) and a fake
👉 Top 3 Easy-to-Get Cryptocurrency Airdrops for Beginners
As you will have understood, the main tip to follow is to ensure the authenticity of the profile that communicates the airdrop. To do this, Several elements must be taken into account :
- The number of subscribers;
- Members of your subscribed network;
- Post statistics;
- The date the profile was created;
- or even the history of posts.
On the social network X, The official announcement of an airdrop is usually accompanied by a thread indicating the protocol's objective, its roadmap, or even its tokenomics. Conversely, hackers are content to share only the message relating to the airdrop. A simple trick to follow is therefore to check whether an explanatory thread is present or not.
Additionally, there is an easy and quick technique to access the authentic profile of a protocol. All you have to do is go to their website and head to the area relating to their various social networks.. Therefore, you will have access to their accounts and communications without risk.
Beyond these methods, Pocket Universe browser extension plays a vital role in protecting Internet users: it helps prevent many scams thanks to its… [70 % de l’article restant]