On 1 October, 2024, the US Department of the Treasury's Office of Foreign Assets Control (OFAC), the UK's Foreign Commonwealth and Development Office (FCDO), and Australia's Department of Foreign Affairs and Trade (DFAT) concurrently designated members of Evil Corp, a Russia-based cybercrime syndicate responsible for the development and distribution of Dridex malware. The US Department of Justice also unsealed an indictment charging one Evil Corp member in connection with its use of BitPaymer ransomware targeting victims in the United States.
Evil Corp stands out not only for the magnitude of its cybercrime — its malware has infected computers and harvested login credentials that has resulted in more than $100 million in theft from hundreds of banks and other financial institutions worldwide — but also for its deep roots in Russia's cybercrime landscape.
Below, we'll take a closer look at Evil Corp's sanctions, its relationship to cybercriminal group Lockbit and the Russian state, and more.
Global disruption of Evil Corp
The October 2024 joint designations complement a 2019 OFAC designation that targeted Evil Corp's founding leader, Maksim Yakubets, and more than a dozen members, facilitators, and companies affiliated with the group, including Evil Corp admin responsible for Dridex, Igor Turashev, and Evil Corp financial facilitator Denis Gusev.
In the UK, the FCDO designated 16 individuals, including Maksim Yakubets and seven Evil Corp individuals designated by OFAC in 2019. One of the individuals sanctioned in 2019 is Aleksandr Viktorovich Ryzhenkov, who worked closely with Yakubets to develop some of Evil Corp's most prolific ransomware strains. Notably, Ryzhenkov has also been identified as a Lockbit affiliate. In addition to the FCDO's efforts, the UK's National Crime Agency (NCA) published “Evil Corp: Behind the Screens,” an extensive investigation into the group.
In Australia, DFAT sanctioned Yakubets, Turashev, and Ryzhenkov.
Finally, several European law enforcement agencies took coordinated action to disrupt Lockbit actors. A suspected Lockbit developer was arrested at the request of the French authorities; the British authorities arrested two individuals for supporting the activity of a LockBit affiliate; and Spanish officers seized nine servers, part of Lockbit's ransomware infrastructure, and arrested an administrator of a bulletproof hosting service used by Lockbit.
Evil Corp's connections to Lockbit
As we've previously covered, Evil Corp's and Lockbit's activities have overlapped on-chain. Specifically, rebranded ransomware strains associated with Evil Corp and cryptocurrency clusters belonging to Lockbit have used the same deposit addresses at centralized exchanges, as shown in the below Chainalysis Reactor graph.
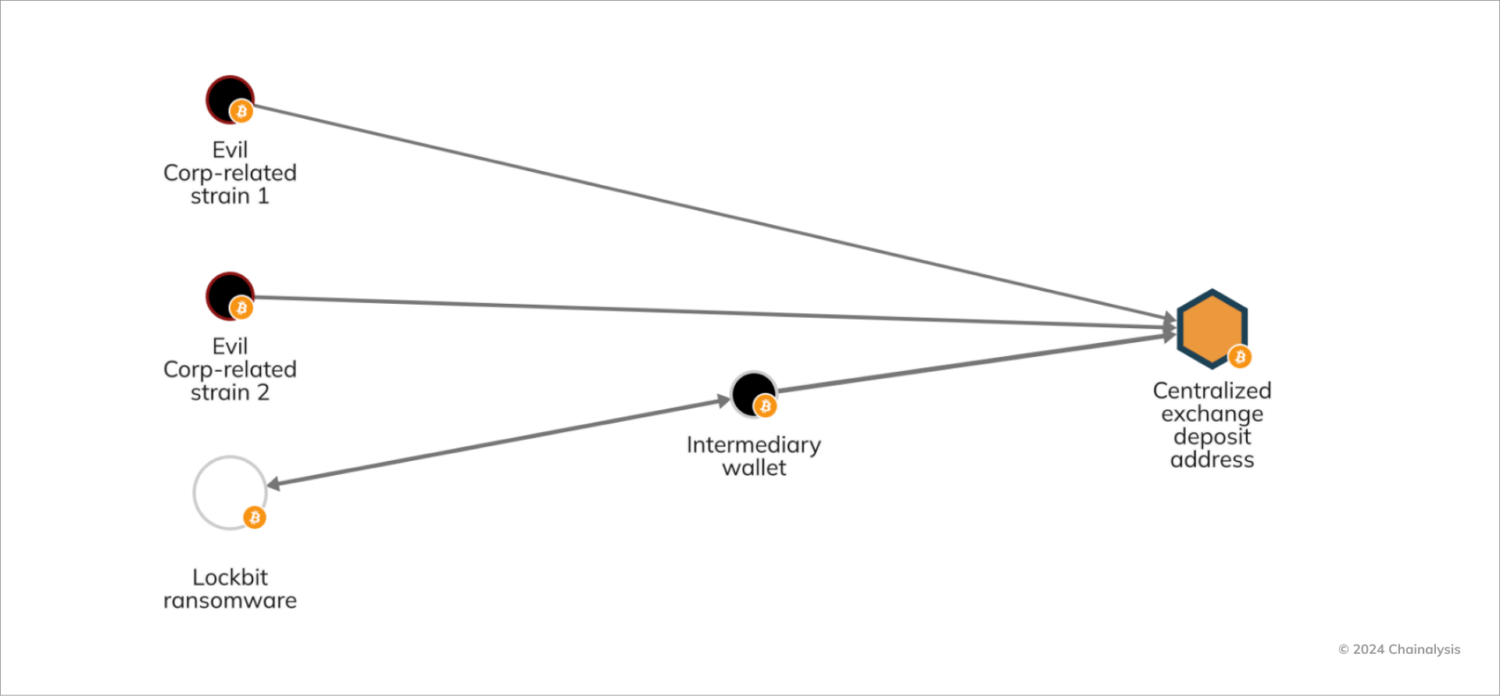
This on-chain overlap is consistent with a 2022 Mandiant report discussing Evil Corp's use of Lockbit as part of its efforts to rebrand and minimize affiliation with sanctioned entities.
Robust family ties, internally and to the security services
A core aspect of Evil Corp's operations is that many of the same family members appear to be involved in its activities. For instance, the US Treasury Department noted in its original 2019 designation that Maksim Yakubets had worked for Russia's Federal Security Service (FSB) and as of 2018, was in the process of obtaining a license to work with Russian classified information from the FSB. Eduard Benderskiy — Yakubets' father-in-law and a former FSB Spetsnaz (Special Forces) officer — was also designated on October 1, 2024 by the US Treasury.
According to the designation, Benderskiy was a key enabler of Evil Corp's relationship with the Russian state, leveraging his status and contacts to coordinate activities between Evil Corp and Russian intelligence officials. In addition, Maksim's father Viktor was designated by the Treasury, FCDO, and DFAT on October 1, 2024, and Artem Yakubets — likely Maksim's brother, given their identical middle name (Viktorovich) and place of birth (Polonnoye, Ukraine) — was also designated in 2019 for being a core Evil Corp member and providing material assistance to the group.
Beyond these connections, Sergey Ryzhenkov — who was designated by OFAC, FCDO, and DFAT — is likely related to Yakubets's right-hand man Aleksandr Ryzhenkov, given their shared middle name.
Global coordination to take down Russia-based cybercriminals
The above actions are part of a larger campaign of coordinated, multilateral actions to disrupt Russia-based cybercriminals, many of whom use crypto to conduct their illicit activities. Other recent examples of this include the German Federal Criminal Police (BKA)'s takedown of 47 Russian no-KYC exchanges, and OFAC's designation of Russian Exchange Cryptex and Fraud Shop Facilitator UAPS, in coordination with a takedown of these services by Dutch and US law enforcement.
As William Lyne, Head of Cyber Intelligence at the NCA stated, “Evil Corp is a stark reminder of how cybercriminals are continuously evolving their tactics. As Evil Corp moved to utilizing ransomware, cryptocurrencies became an important element of their business model. However, with the data obtained from the LockBit group, the NCA have been able to use a range of tools and capabilities to track and attribute affiliates, including an Evil Corp member. This included harnessing the inherent transparency and traceability in the blockchain. The activity delivered on October 1st shows the power of partnerships and collaboration in disrupting threat actors responsible for harming the UK and our allies.”
These designations, and related arrests and seizures across the United States, United Kingdom, and Australia are likely to generate follow-ups related to additional disruptions and prosecutions. We will continue to provide updates on these cybercriminals and related entities when available.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.