On September 19, 2024, the German Federal Criminal Police (BKA) seized the infrastructure of 47 Russian-language no-KYC (Know Your Customer) cryptocurrency exchanges. Dubbed “Operation Final Exchange,” the takedown stands out not only for its breadth, but also for the light it has shined on the central role instant-swap style no-KYC exchanges play in facilitating on-chain cybercrime.
As their name suggests, no-KYC exchanges have no known process for collecting customer information before allowing any level of deposit or withdrawal. They do not require a name, phone number, or email address, and make no attempt to verify this information prior to permitting transactions. As such, these services allow a range of cybercriminals to abuse their services without KYC controls to identify or disrupt illicit activity. The BKA's Operation Final Exchange landing page calls out ransomware affiliates, botnet operators, and darknet vendors as users of the 47 targeted exchanges. Beyond that, these services offered fiat on- and off-ramping for sanctioned Russian banks, creating an avenue for sanctions evasion.
Below, we'll dive into these exchanges' on-chain activity, explore their nexus to sanctioned Russian banks, and discuss the disruption's implications.
Who are these 47 No KYC Exchanges?
Our data reveals interesting patterns about the services targeted by the BKA, with robust direct and indirect exposure to various illicit services. At least seventeen of the exchanges saw a month of more than 50% of direct inflows from illicit sources. At least twelve saw a month where more than 30% of direct inflows were from darknet marketplaces (DNMs). At least six saw at least one month where stolen funds comprised more than 30% of total direct inflows. At least five had at least one month where more than 30% of indirect inflows were from sanctioned entities.
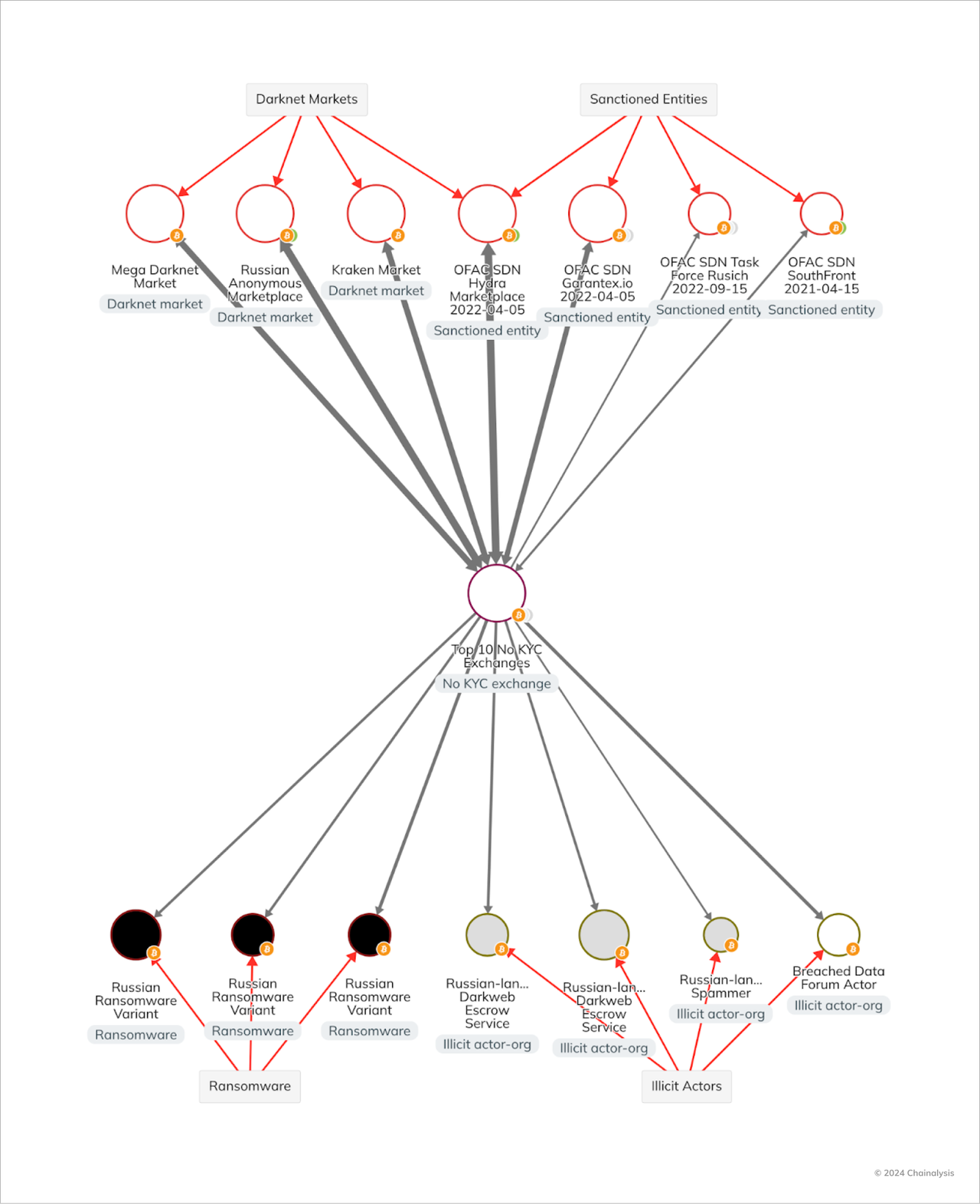
This exposure demonstrates that for many of these services, laundering illicit funds was a substantial part of their businesses. Indeed, as depicted in the below Chainalysis Crypto Investigations graph, the top ten services targeted by the BKA transacted with a broad array of illicit services, including, but not limited to, sanctioned entities, ransomware actors, DNMs, and darkweb escrow and breached data brokers.
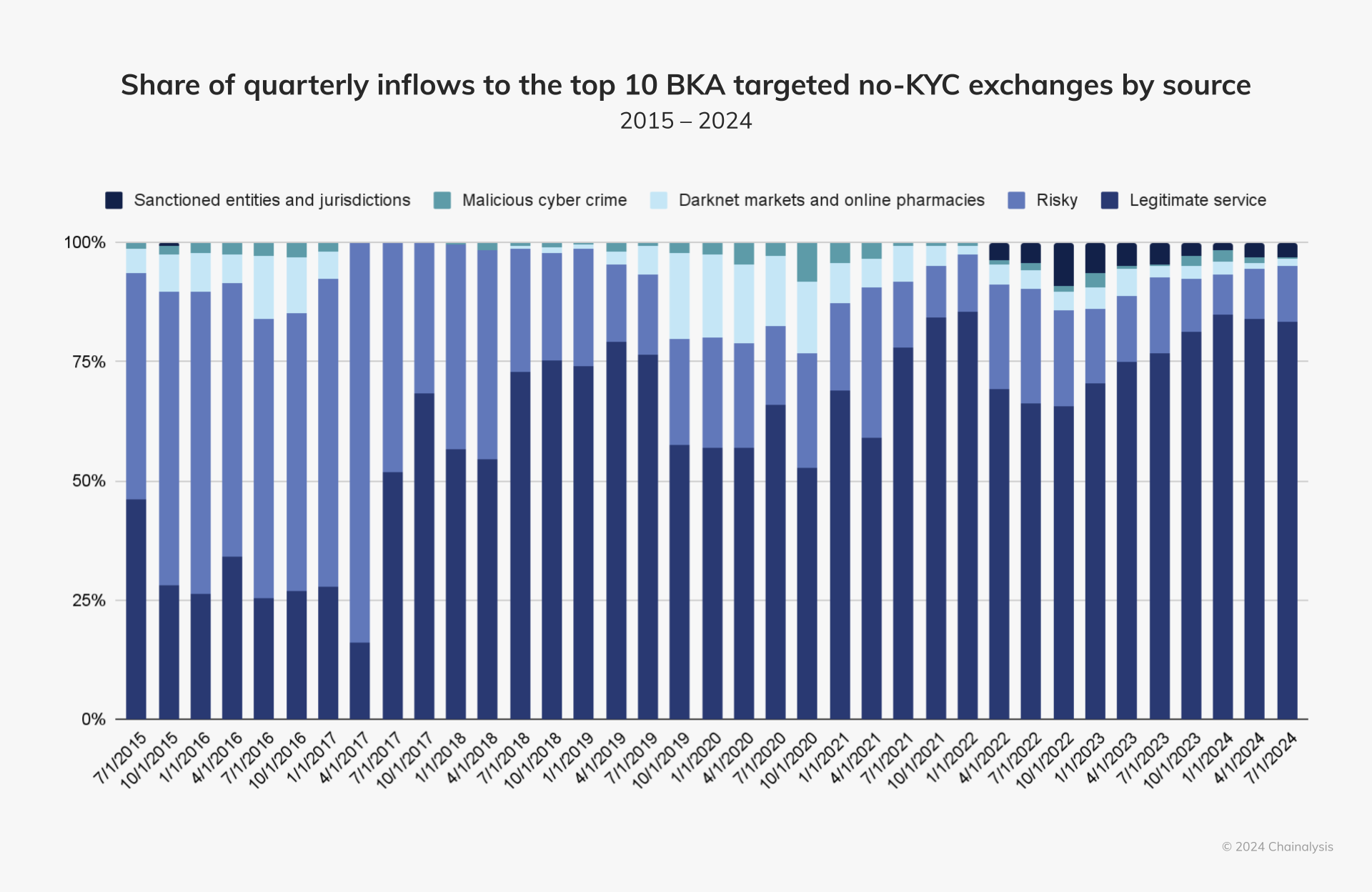
The chart below shows the quarterly inflows to the top ten exchanges taken down by the BKA. These services received value from a variety of sources, including periods of significant inflows from drug-related DNMs, online pharmacies, malicious cybercriminals such as ransomware gangs, and funds stolen in heists and scams.
There is also a notable increase over time in the proportion of inflows from legitimate sources, notably centralized exchanges. While this change to the composition of inflows might in other circumstances suggest that the services were in the process of cleaning up their platforms, the reality is likely more complicated. In this case, the increased inflows from otherwise legitimate sources most likely represent the growing use of these services for sanctions evasion on the part of Russian nationals, who are likely trying to leverage these no KYC exchanges to evade sanctions on Russian banks.
How do these services work?
These services operate as instant-swap style services, in which users, without providing any personal information or going through any verification process, can swap from one currency to another. The offerings include crypto-to-crypto and fiat-to-crypto swaps, allowing users to instantly exchange popular cryptocurrencies and stablecoins, or to connect their bank account to on-/off-ramp fiat to crypto instantly.
As with other categories of the illicit crypto ecosystem, we have observed that no KYC exchanges, particularly those targeted by the BKA, often have overlapping or similar on-chain infrastructure, and in some instances even share off-chain networks, such as website shells , employees and administrators, physical locations, and ownership structures, to name a few. More often than not, these websites have no affiliated company incorporation, registration, phone numbers, physical addresses, or any indicator of jurisdictional operation. Unlike other high-risk and illicit services, most of these services do not have a social media presence, instead offering users the ability to interface with a bot on their homepages. Despite using servers based in Germany, these services cater primarily to a Russian clientele, as suggested by their default language settings in Russian and information on banking services for fiat transactions provided by sanctioned Russian banks, such as Sberbank.
Connectivity to sanctioned Russian banks
Many of the 47 no KYC exchanges were Russian-language platforms offering fiat-to-crypto and crypto-to-crypto instant exchange services. As we covered in our recent analysis of Russia's new cryptocurrency legislation, Russian-language instant exchangers can be exploited to quickly move fiat currency from sanctioned Russian banks to specified crypto wallets, enabling entities to evade sanctions. Given the dramatically increased sanctions pressure on Russian banks following the full-scale invasion of Ukraine in February 2022, instant exchangers have emerged as a convenient way to on- or off-ramp funds for sanctioned banks. Of the 47 no KYC exchanges targeted in Operation Final Exchange, all that we have identified on-chain accepted on- and off-ramping with sanctioned Russian banks.
Breadth of disruption likely to generate actionable inroads
Most of the exchanges targeted by BKA have been active since 2021 or before, and the top three in terms of transactions processed – Xchange.cash, 60cek.org, and Bankcomat.com – have been active since 2016 or before, according to the Operation Final Exchange landing page. The longevity of these services suggests a substantial portion of customers affected will need to establish alternative financial facilitation and laundering pathways.
The disruption's impact is likely to extend far beyond the no KYC exchanges targeted. As the BKA stated, it is now in possession of these exchanges' development, production, and backup servers, as well as transactional details, registration data, and IP addresses. This data will likely be instrumental in generating follow-on leads for the BKA and key international law enforcement partners in the months to come. We continue to track this phenomenon closely and will flag new no KYC exchanges that emerge as key players in this space.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient's use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.